Documentation
Get detailed guidance on platform features




In addition to our Zero Trust Architecture, we’ve incorporated several other security aspects into our system
Data Encryption
At XMPro, we use advanced encryption methods to protect your data both at rest and in transit. This ensures that your data remains secure and unreadable to unauthorized users.
Regular Audits
We conduct regular security audits to identify and rectify any potential vulnerabilities. This proactive approach helps us stay ahead of emerging threats.
Secure Development Practices
Our development team follows secure coding practices to prevent common security risks such as SQL injection, cross-site scripting, and more.
Incident Response Plan
In the event of a security incident, we have a comprehensive response plan in place to minimize damage and recover quickly.
User Training
We believe that security is everyone’s responsibility. That’s why we provide regular training to our users on best practices for data security.
In the rapidly evolving digital landscape, organizations seek technology solutions that offer not only robust performance but also the flexibility to adapt to changing business needs and technological advancements. XMPro stands at the forefront of this demand, offering unparalleled deployment capabilities that span the entire cloud to edge continuum.
XMPro’s flexible deployment architecture offers a suite of options designed to meet the diverse needs of modern enterprises. Understanding the nuances of each deployment option can help organizations tailor their XMPro integration to achieve optimal performance, security, and scalability.
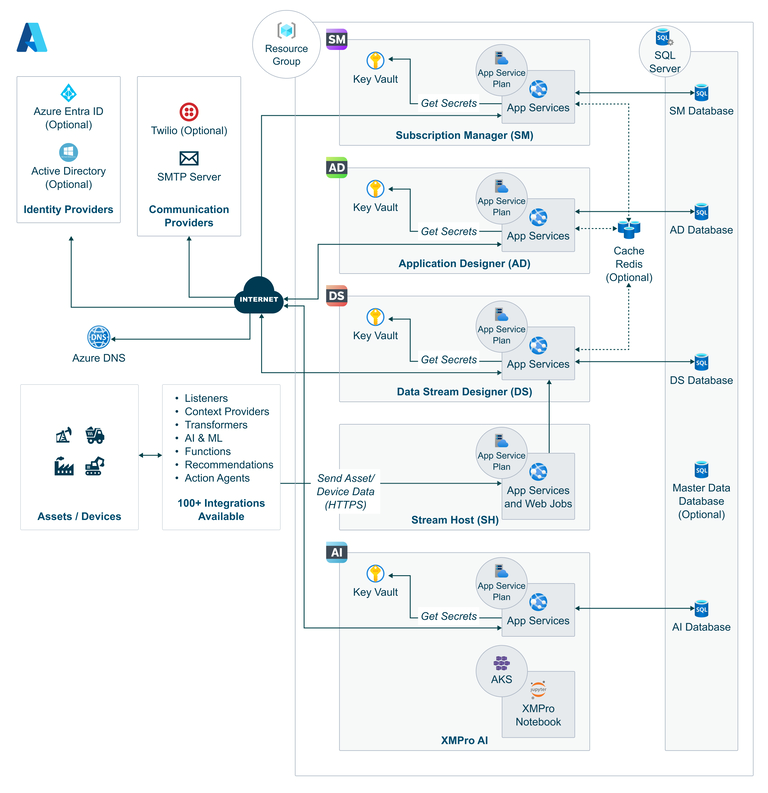
Fig 1: Example XMPro architecture in Azure Cloud Deployment
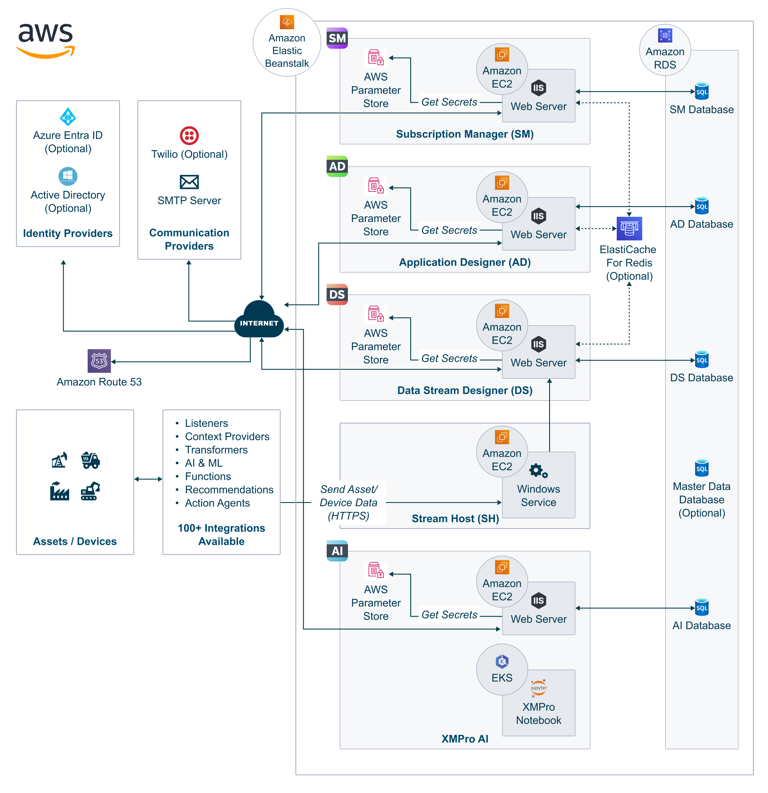
Fig 2: Example XMPro architecture in AWS

As part of the Dell Validated Design (DVD) for Manufacturing Edge, XMPro runs an advanced edge solution to empower manufacturers to deploy, manage, and scale advanced Digital Twin technologies.
Depending on the Use Case, XMPro can run on different Topologies. Often a blended approach with some components of our platform running on both yields.
Examples:

XMPro, as a validated Independent Software Vendor (ISV) for Dell’s Validated Design for Manufacturing Edge, stands at the forefront of driving innovation and efficiency in smart manufacturing. This collaboration underscores the strategic alignment between XMPro’s agile software solutions and Dell’s comprehensive, validated manufacturing edge solutions. These solutions are engineered to deliver the speed, scalability, and resiliency essential for achieving superior smart manufacturing outcomes.
XMPro platform integrates between components via API requests over HTTPS. The Platform has a large and growing number of custom Connectors and Plugins that can be used to integrate to 3rd party systems. These can be added by an administrator at their discretion and monitored and managed through a centralized view.
This ever-growing list of integrations can be viewed here Integrations

The XMPro platform features an Out-of-the-box Role Based Access Control (RBAC) mechanism that can be customized further using Product Rights. This means that an “Admin Role” can have multiple access levels, which can be applied to artifacts generated within the platform. Moreover, these Roles can be managed through third-party identity providers that facilitate Single Sign-On (SSO).
Users are managed via a least-privilege access approach, and all exposed functionality is restricted by just-in-time and just-enough access protocols. The platform also offers Automatic Registration Approval Flows to simplify the registration process.

In today’s digital age, data security is paramount. At XMPro, we understand the importance of protecting your data. That’s why we’ve implemented a Zero Trust Architecture in our system. This approach assumes no trust and verifies every request as though it originates from an open network. Regardless of where the request comes from or what resource it accesses, Zero Trust teaches us to “never trust, always verify.”
What is Zero Trust Architecture?
Zero Trust Architecture is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access.
Why Zero Trust Architecture?
The Zero Trust model shifts the fundamental paradigm of trust from network-based trust to data- and identity-based trust. This shift provides the following benefits:
Strict Identity Verification: Every user and device must prove their identity before accessing our system.
Microsegmentation: We use microsegmentation to break up security perimeters into small zones to maintain separate access for separate parts of the network.
Least Privilege Access: We follow the principle of least privilege (PoLP), ensuring that users have just enough access to perform their job functions.
Multi-factor Authentication: We require multiple pieces of evidence to authenticate a user, making it harder for an attacker to impersonate a user.
AI and Machine Learning: We use industry standards for logging and telemetry supporting AI and machine learning to identify abnormal user behavior and respond to threats in real time through 3rd party providers.
At XMPro, your data security is our top priority. With our comprehensive security measures, including Zero Trust Architecture, we ensure that your data remains secure and private. Trust us to keep your data safe, because with XMPro, it’s Zero Trust, full security.