Security is mentioned in almost every meeting that I have with CIOs, Enterprise Architects, Operational Technology (OT) specialists and the Operations Engineers. It is a high priority topic, and everyone is looking for the holy grail answer to “How do you secure this XYZ IoT project?”.
It is an important consideration in an Industrial IoT project where a compromise in security can lead to catastrophic failure with the potential impact of a Chernobyl or Bhopal. By putting security in the spotlight, we often overlook the bigger issue of the TRUSTWORTHINESS of an industrial IoT solution.
The Industrial Internet Consortium’s (IIC) Vocabulary Technical Report describes trustworthiness as the degree of confidence one has that the system performs as expected with characteristics including safety, security, privacy, reliability and resilience in the face of environmental disruptions, human errors, system faults and attacks. The IIC’s Industrial Internet of Things, Volume G4: Security Framework (IISF) describes this trustworthiness with this simple model.
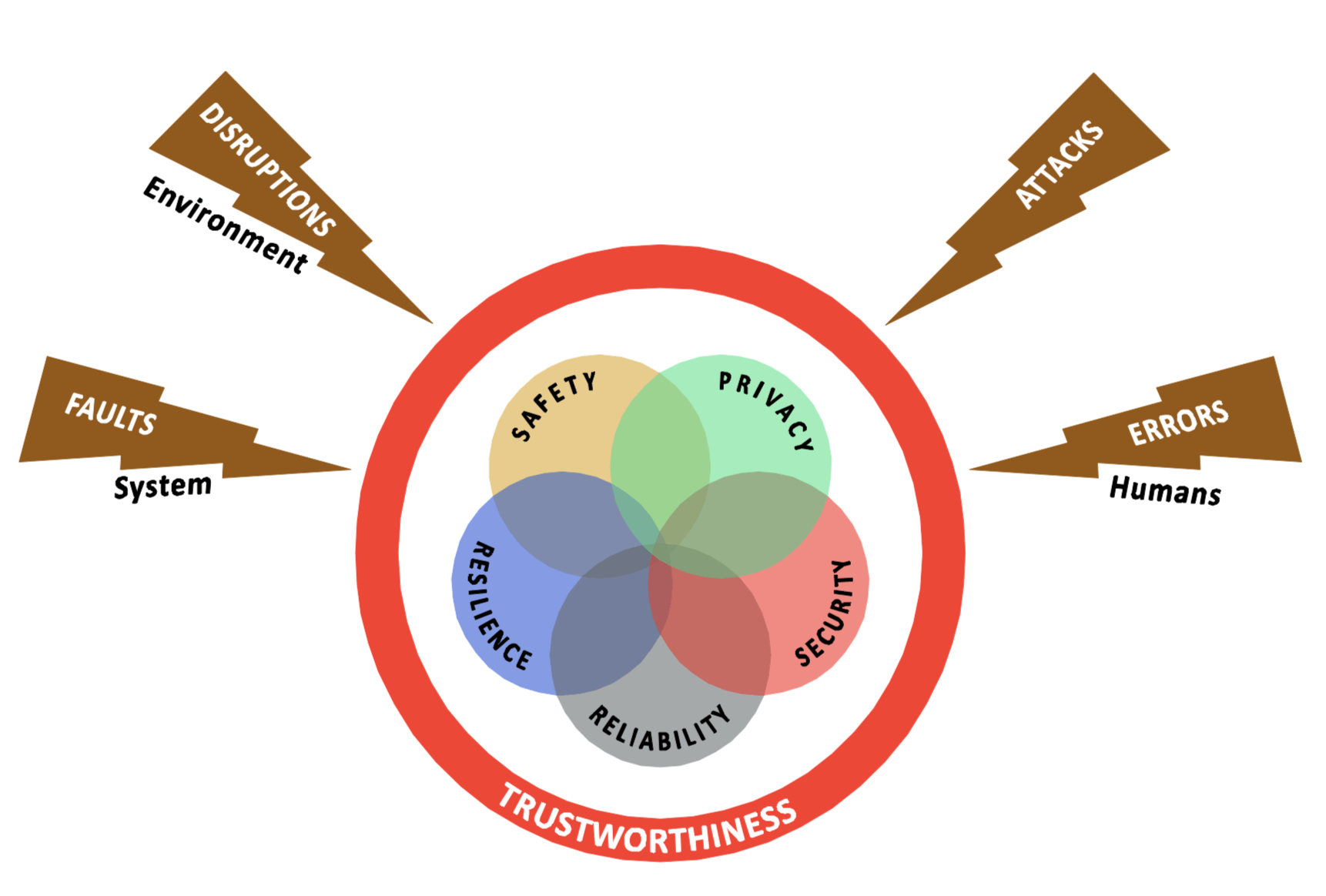
Trustworthiness addresses all the potential risk areas rather than just attacks or intrusions. It questions how we deal with environmental disruptions, human errors and system faults or “bugs” over and above security. Each aspect is described extensively in the IISF, but here are the key definitions:
- Security is the condition of the system being protected from unintended or unauthorized access, change or destruction.
- Safety is the condition of the system operating without causing unacceptable risk of physical injury or damage to the health of people, either directly or indirectly, as a result of damage to property or to the environment.
- Reliability is the ability of a system or component to perform its required functions under stated conditions for a specified period of time.
- Resilience is the emergent property of a system that behaves in a manner to avoid, absorb and manage dynamic adversarial conditions while completing the assigned missions, and reconstitute the operational capabilities after causalities.
- Privacy is the right of an individual or group to control or influence what information related to them may be collected, processed, and stored and by whom, and to whom that information may be disclosed.
Planning and architecting an industrial IoT solution requires that each of these key system characteristics be assured to deliver a trustworthy business solution. This assurance requires the collection and analysis of evidence that supports the design, construction, deployment and test of the system, and its activities in operation. The evidence must support the claim that the right mixture of innate system capabilities and compensating security controls to mitigate risks has been put in place and provide the overall trustworthiness of the IoT system.
The IIC’s Industrial Internet Security Framework (IISF) provides practical guidance to address the assurance requirements of each of the system characteristics from both a business as well as functional and implementation viewpoints. It covers trustworthiness from connectivity at the device level through to the business processes that support the IoT solution.
It is interesting to ask the question “Is security more important that trustworthiness?” in response to “how do you secure your IoT solution?” question and address key system characteristics that were not considered in the hype around IoT security. My answer to the “How do you secure this XYZ IoT project?” question is always the same . . . “let’s design it to be trustworthy, then it will be secure”.
You can get a summary of the IIC frameworks and technical documents here and you can contact us to discuss how to create a trustworthy industrial IoT solution.